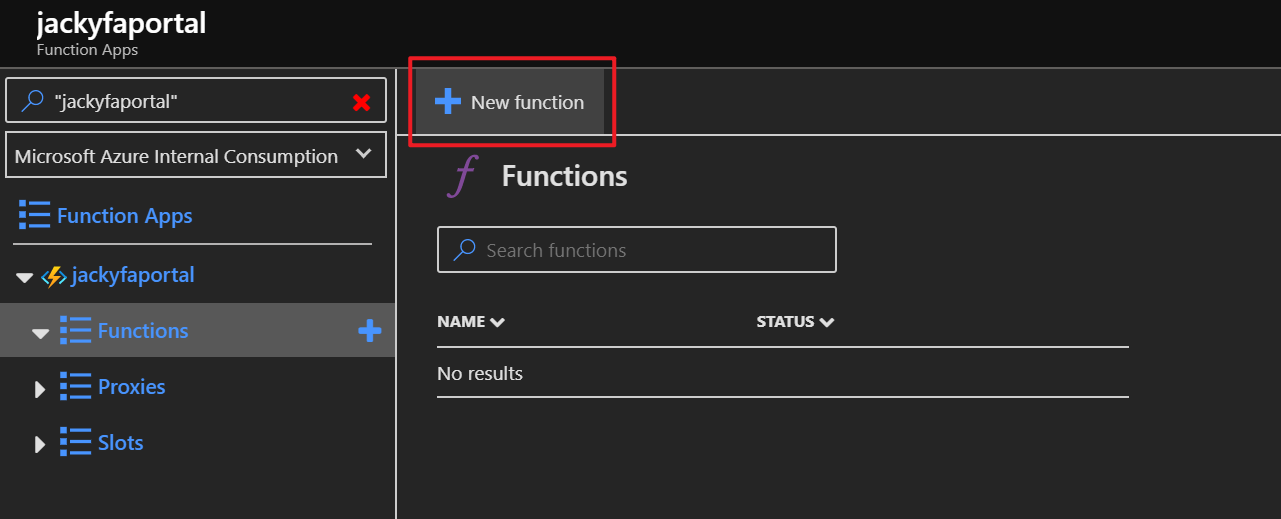
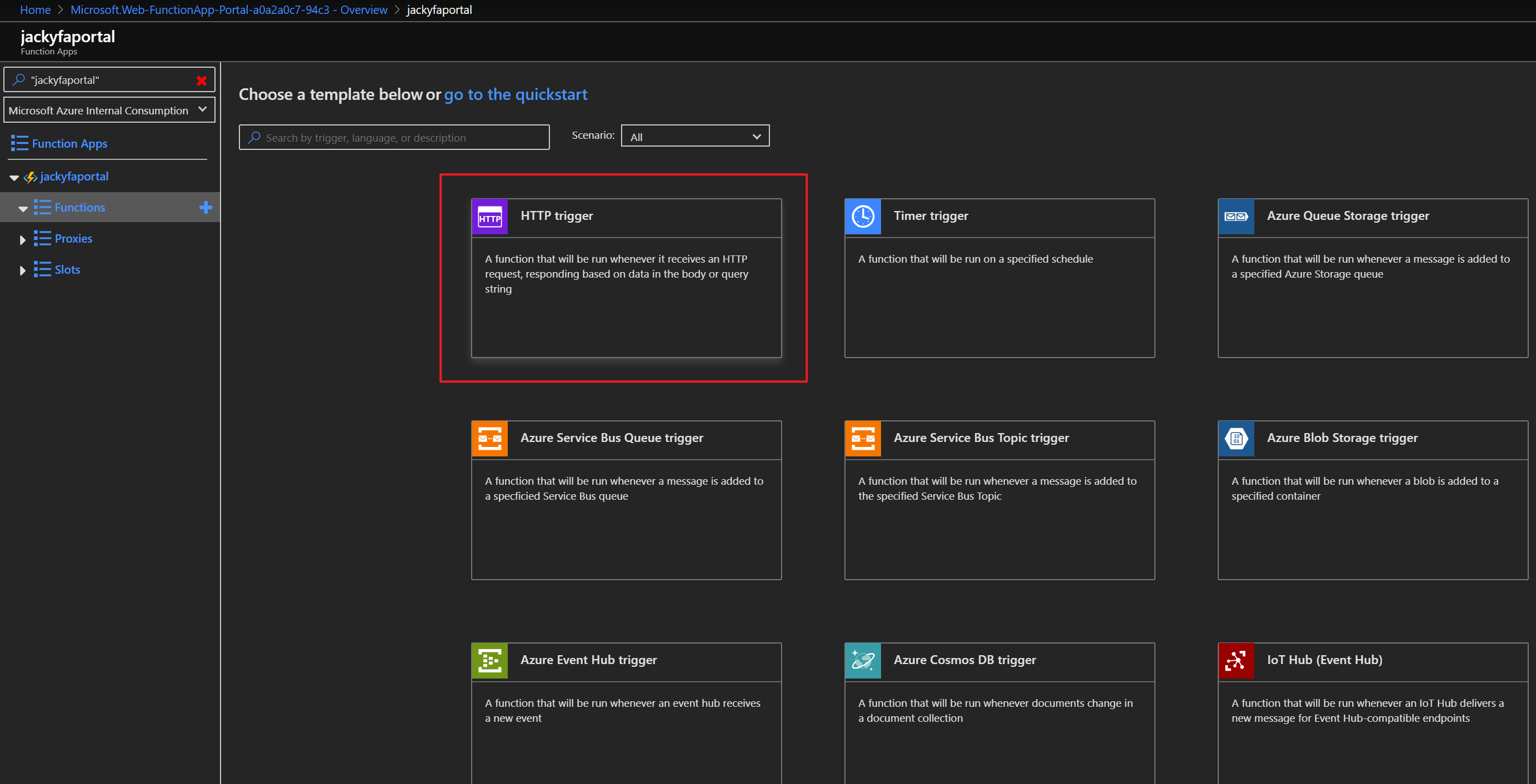
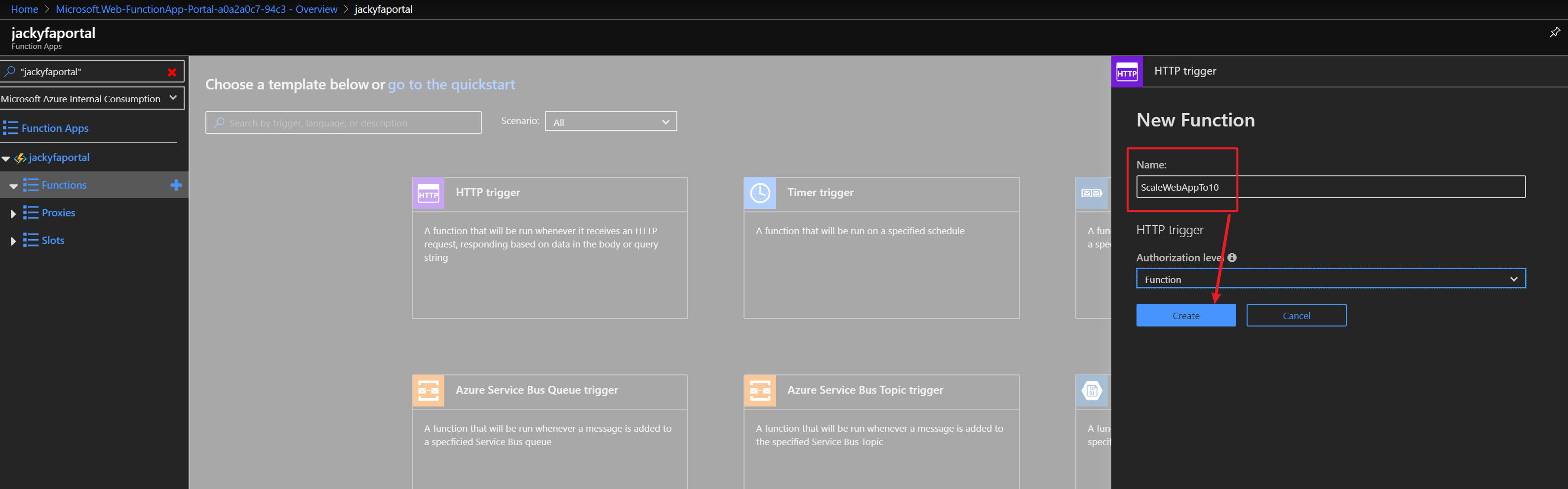
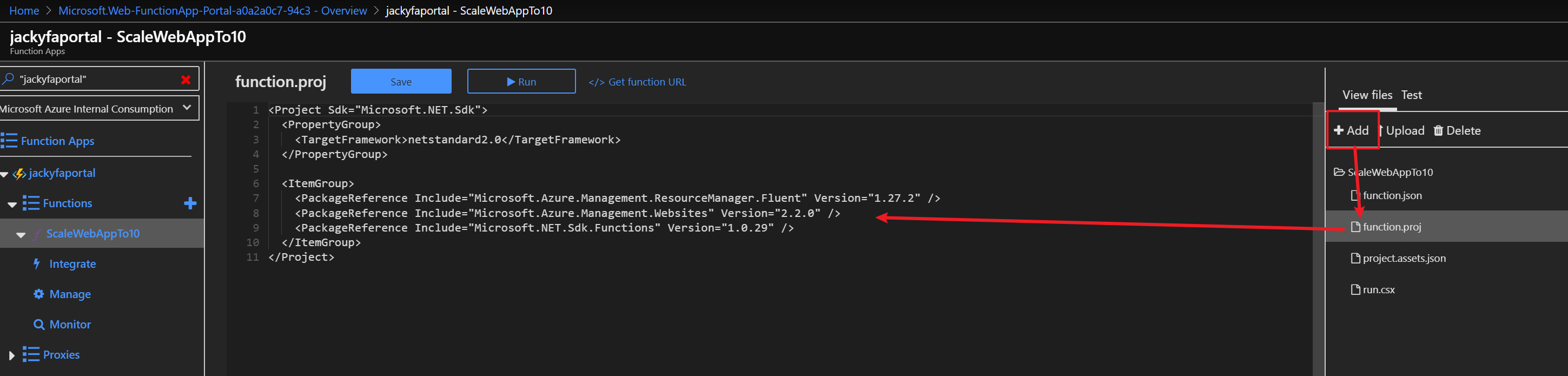
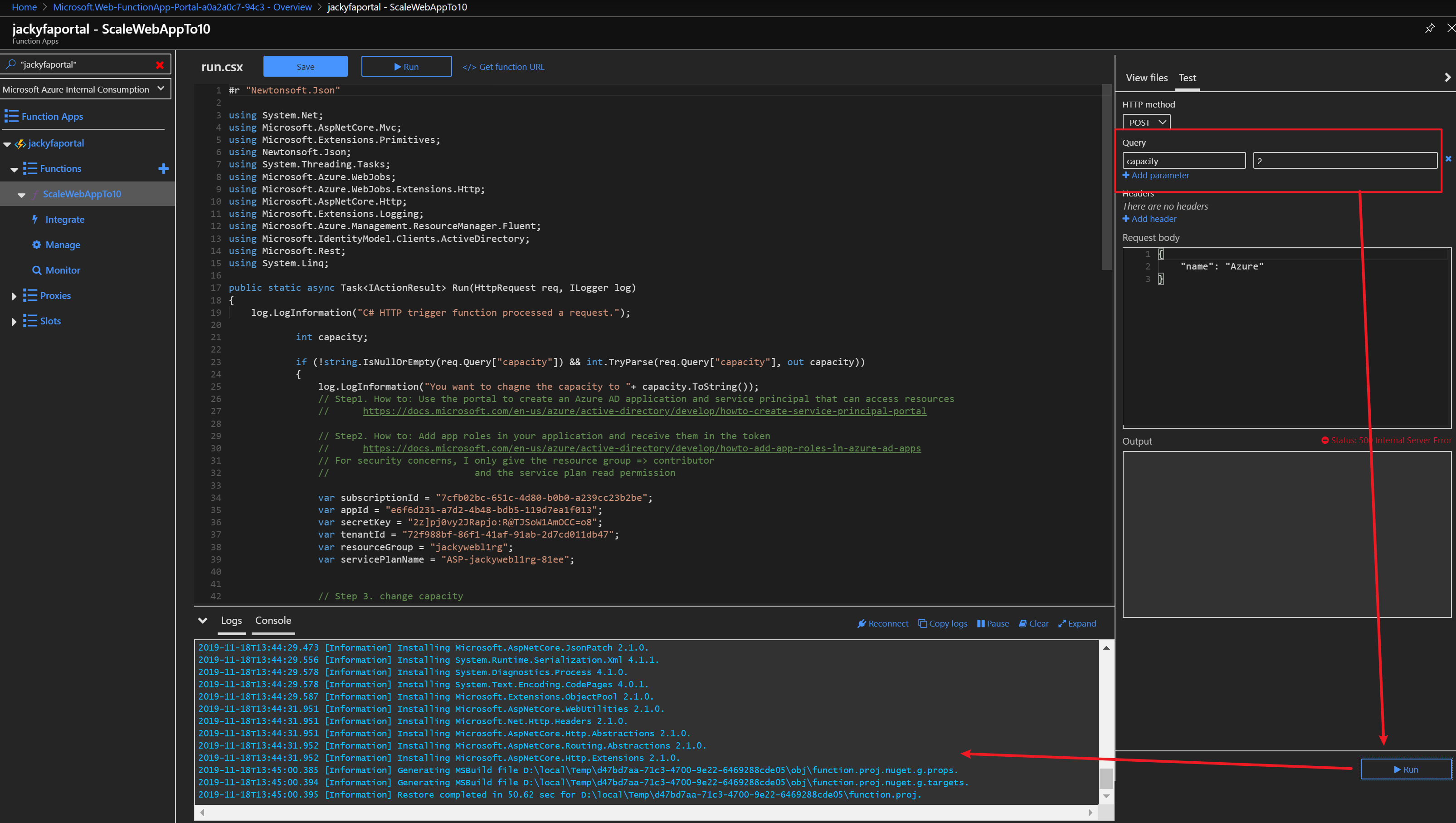
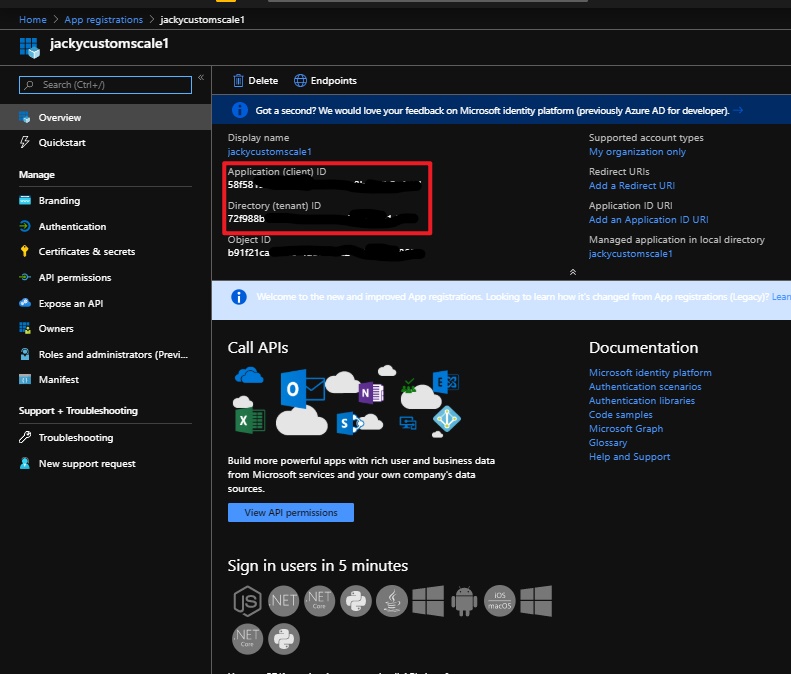
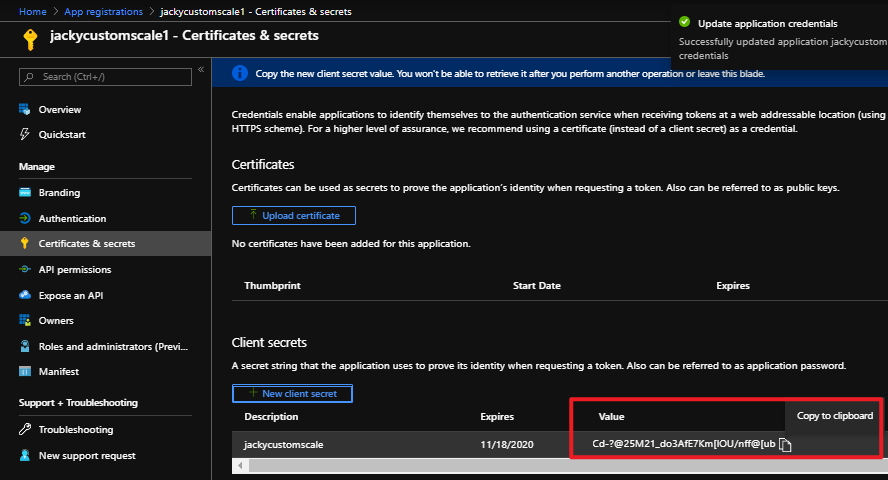
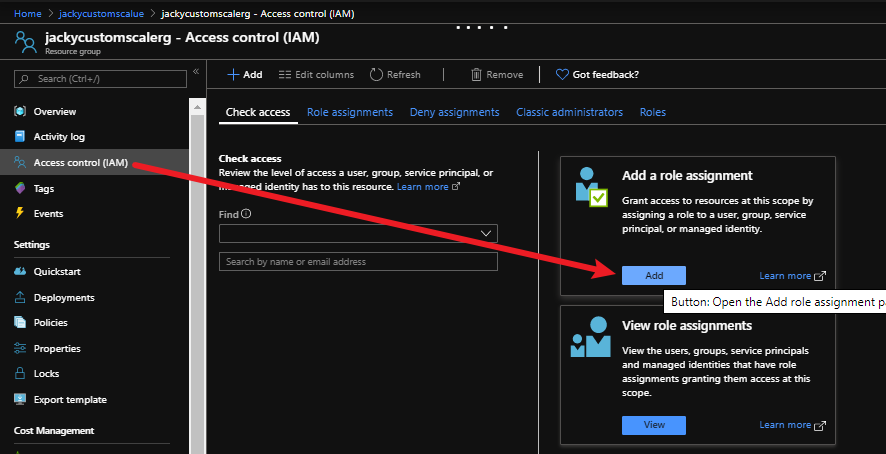
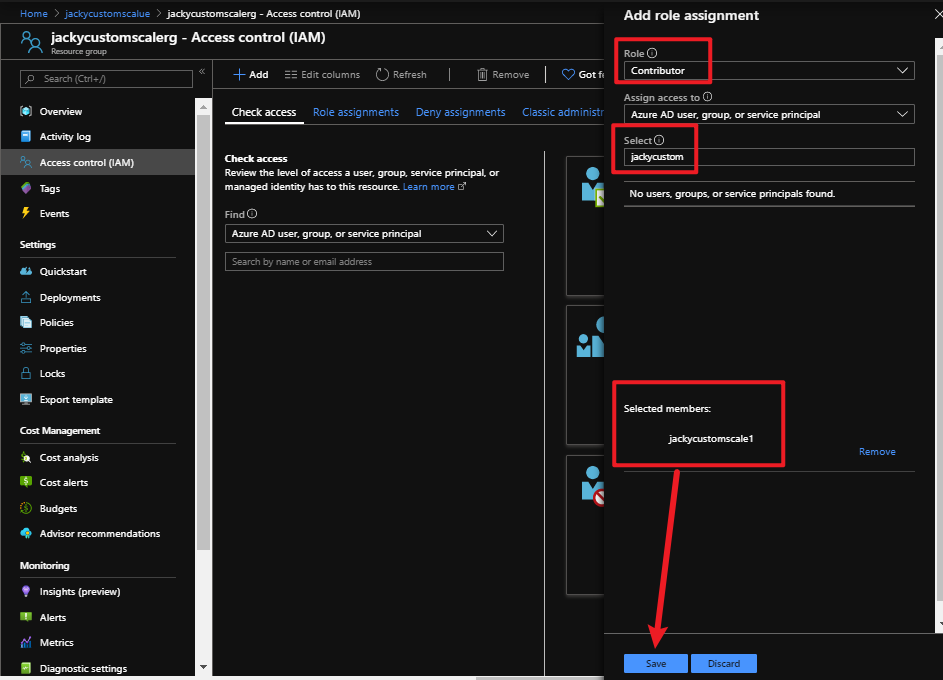
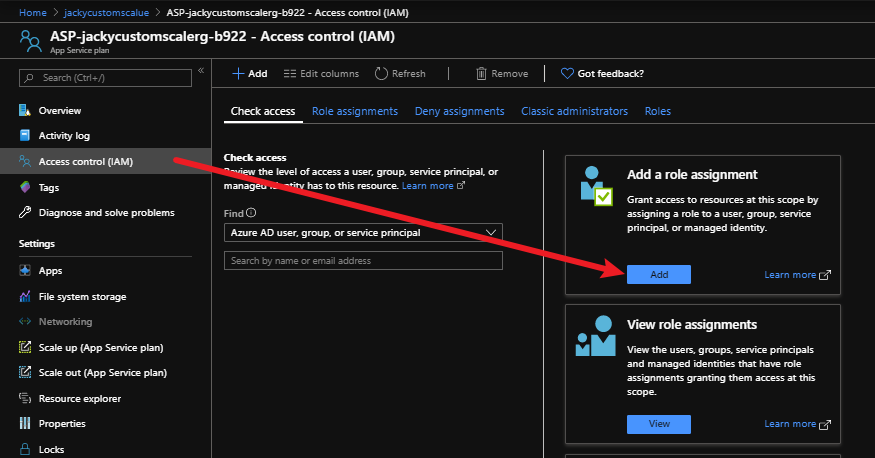
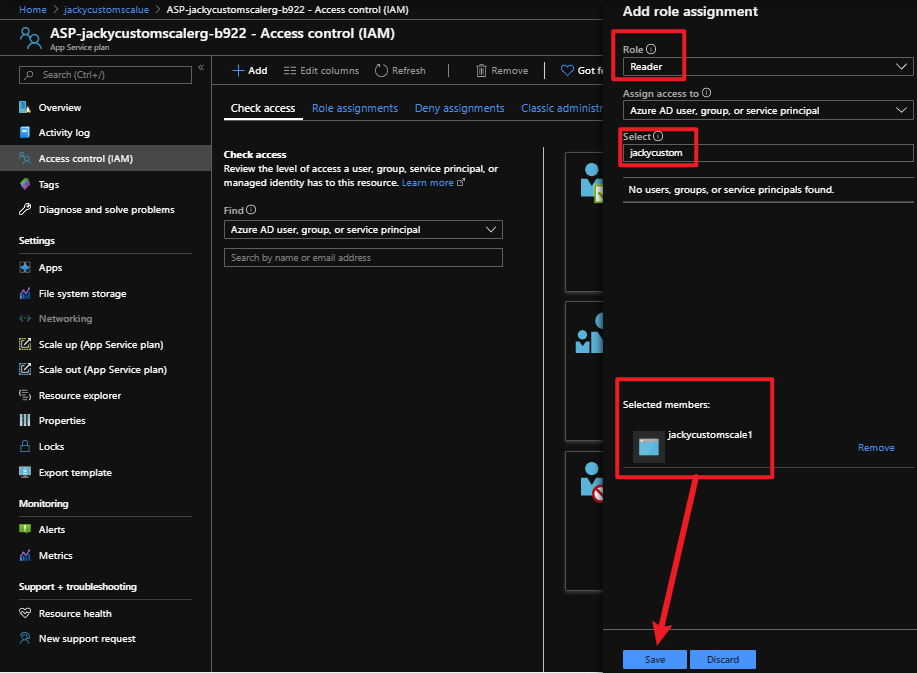
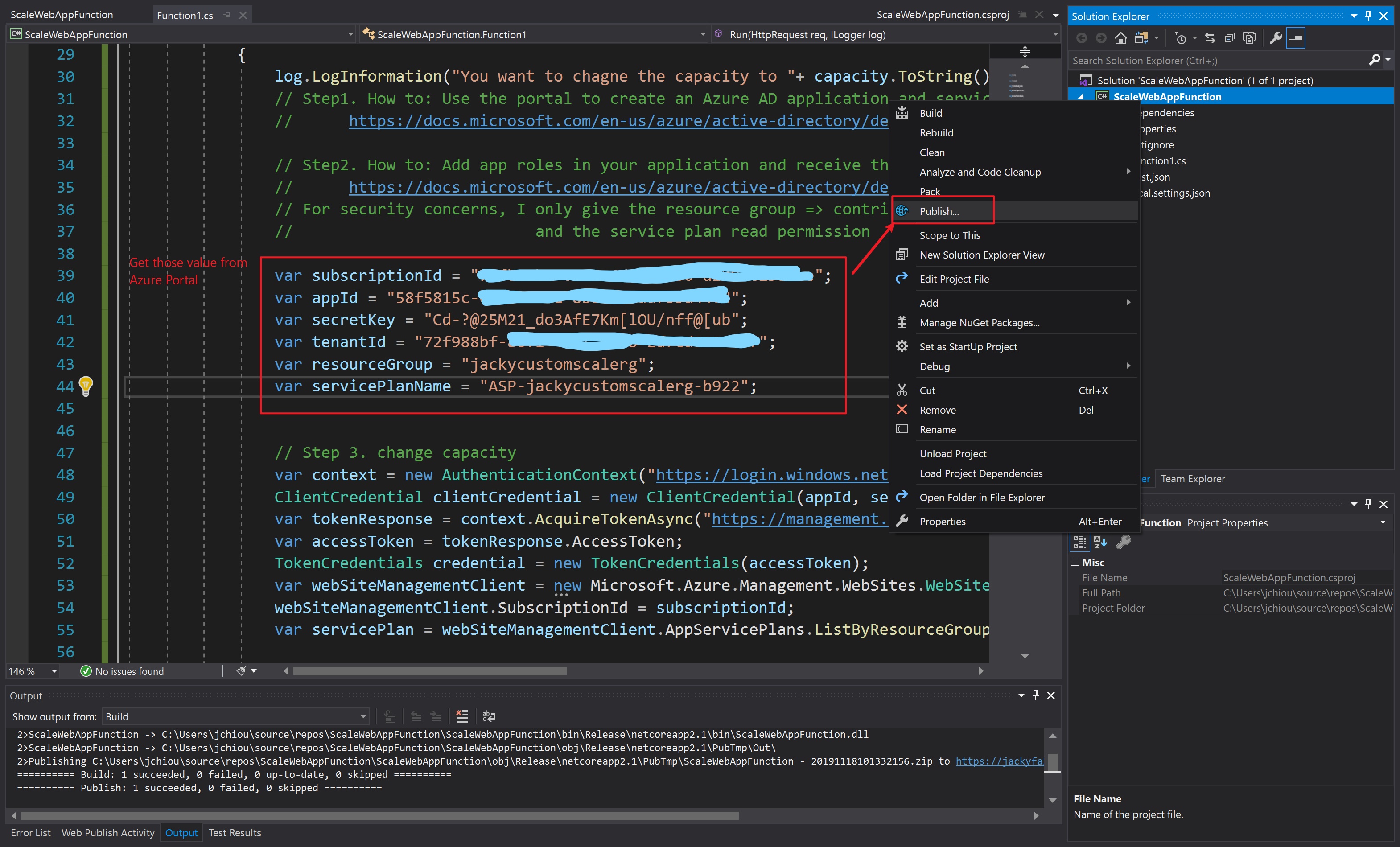
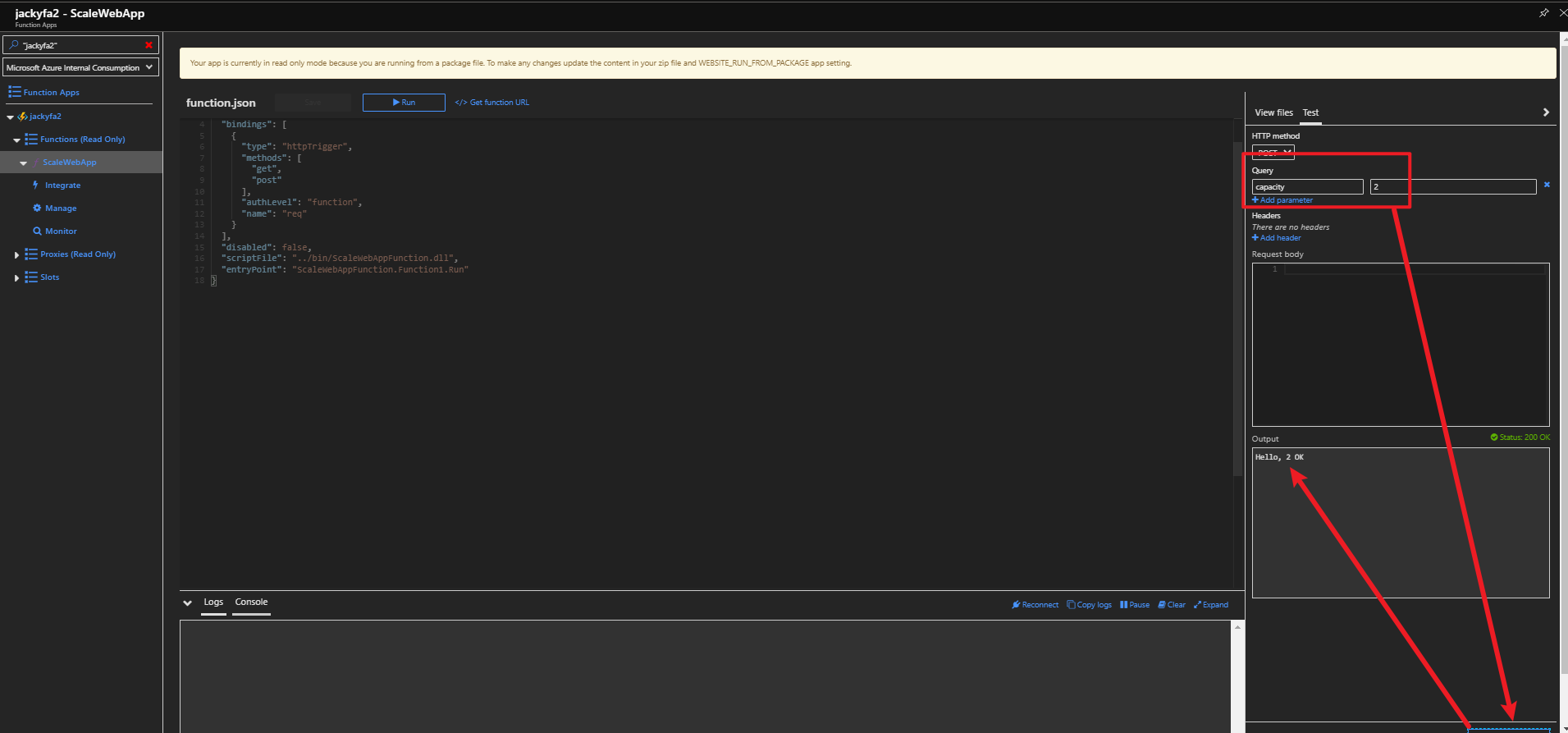
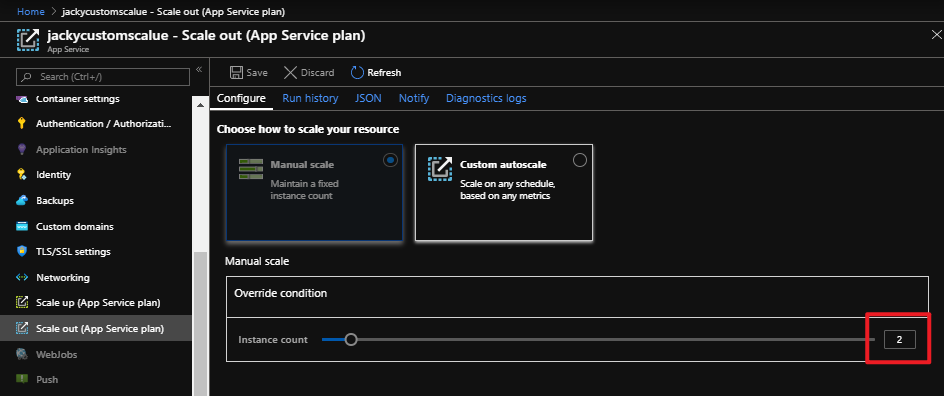
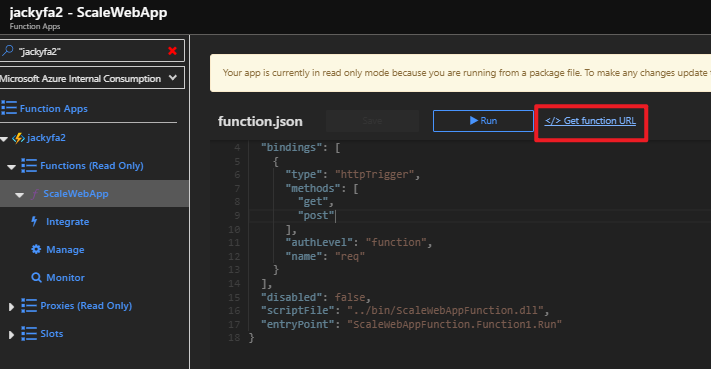
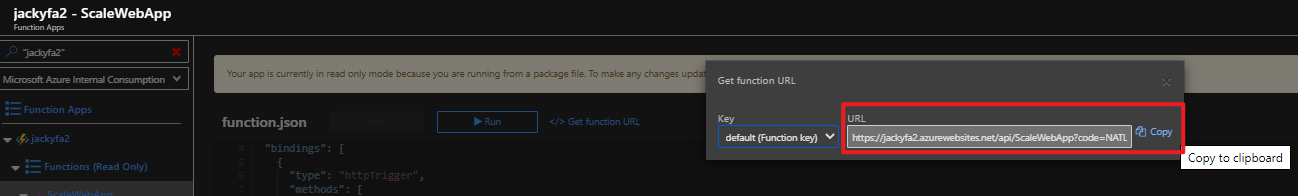
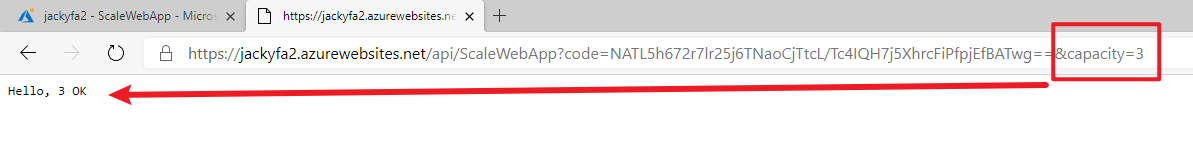
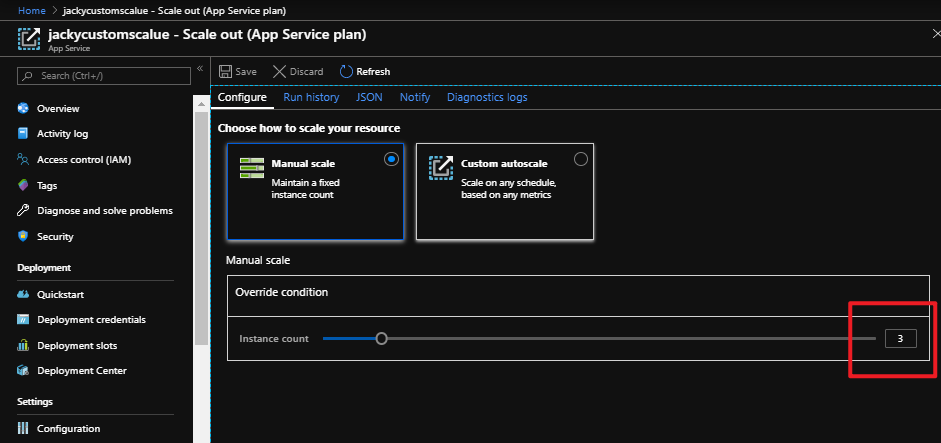
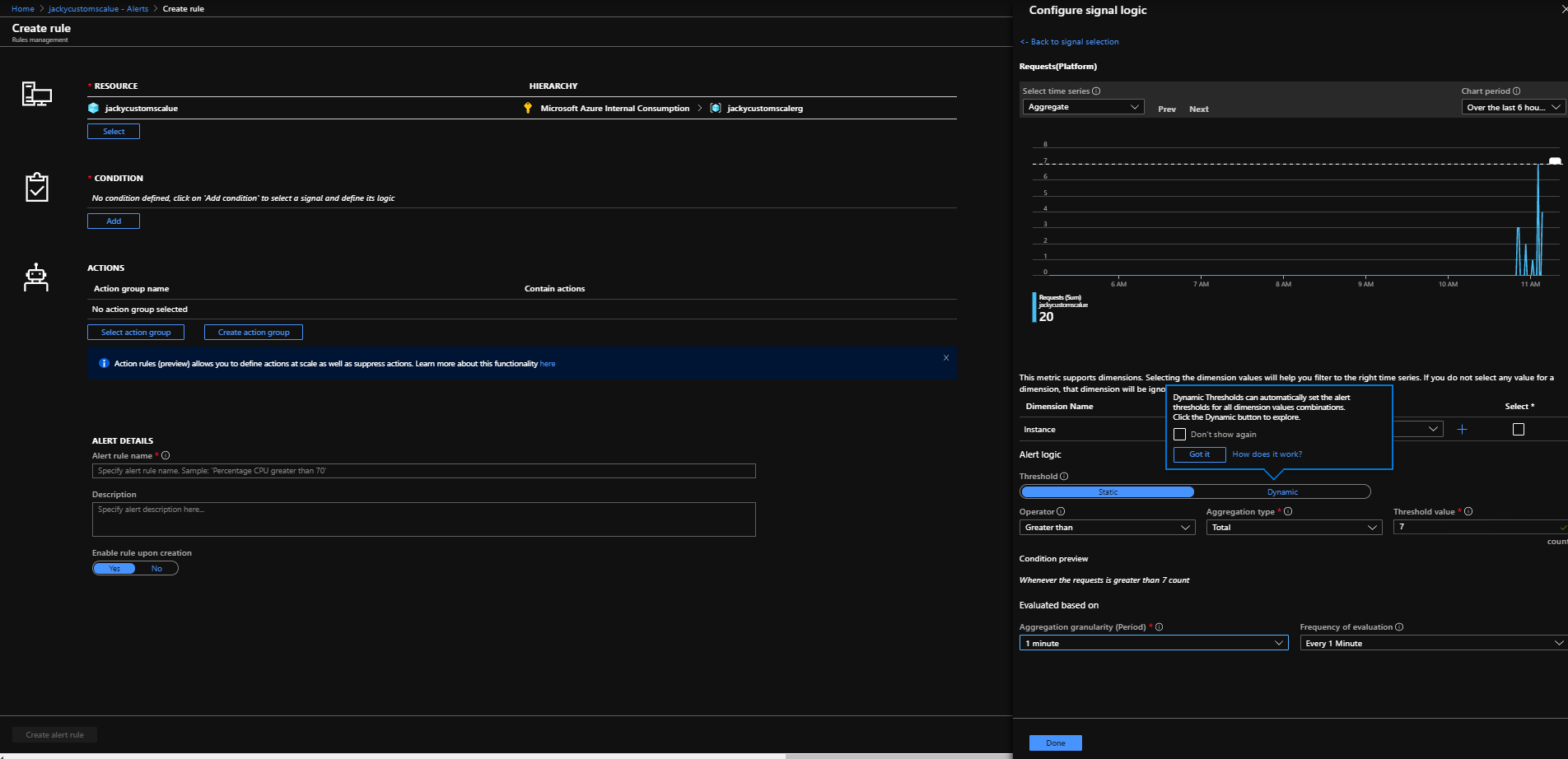
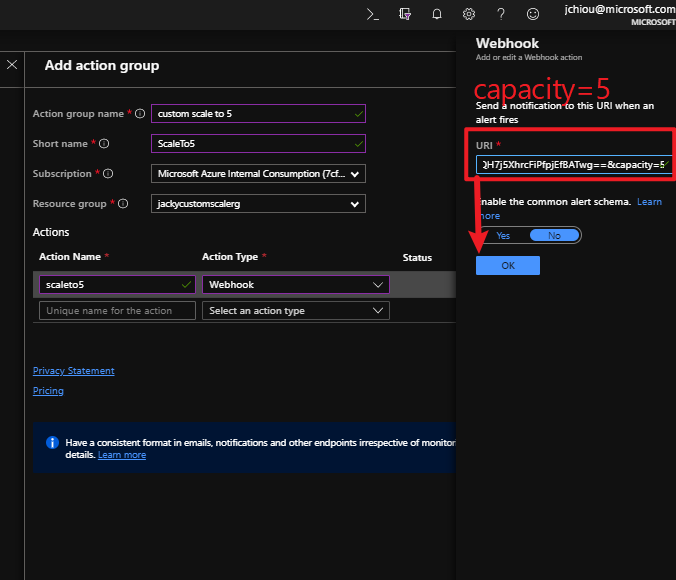
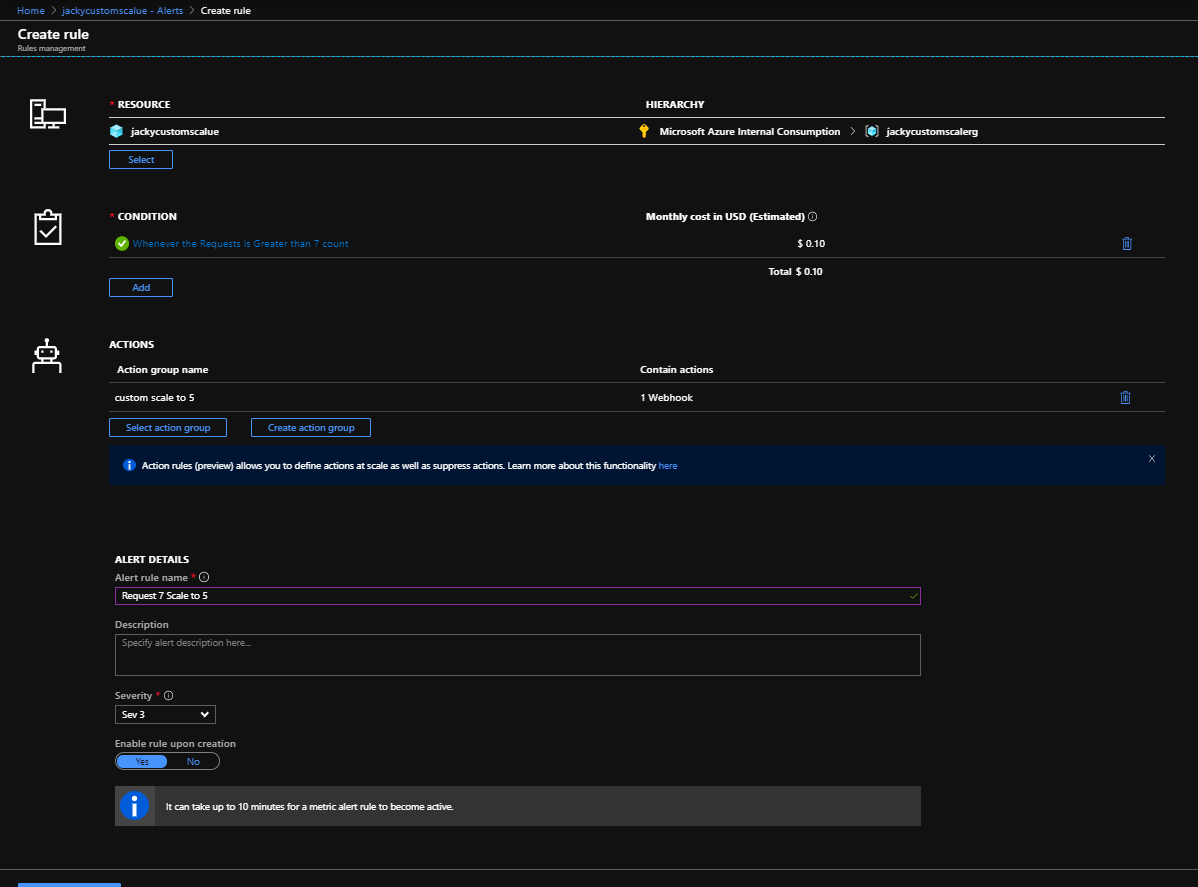
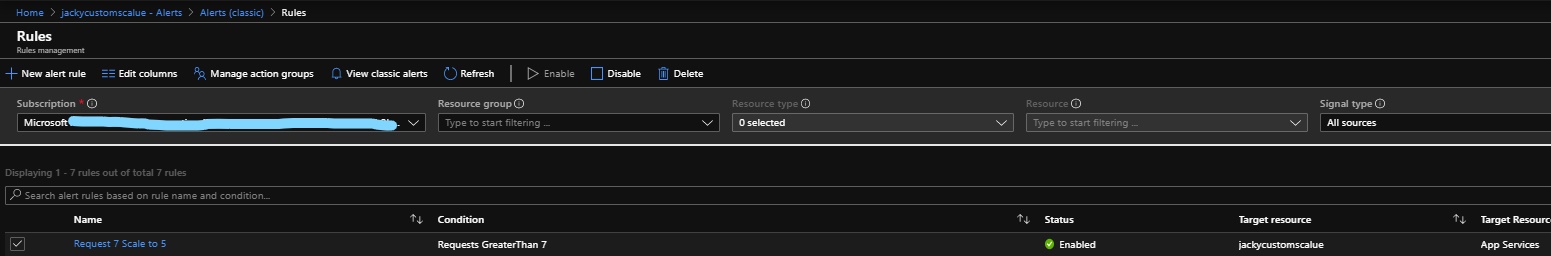
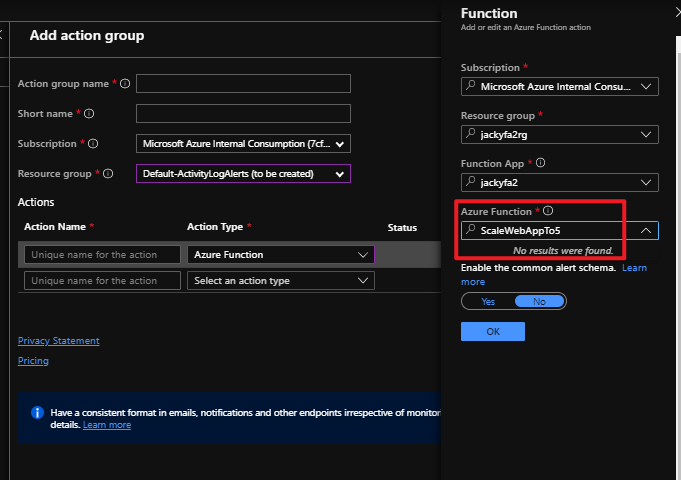
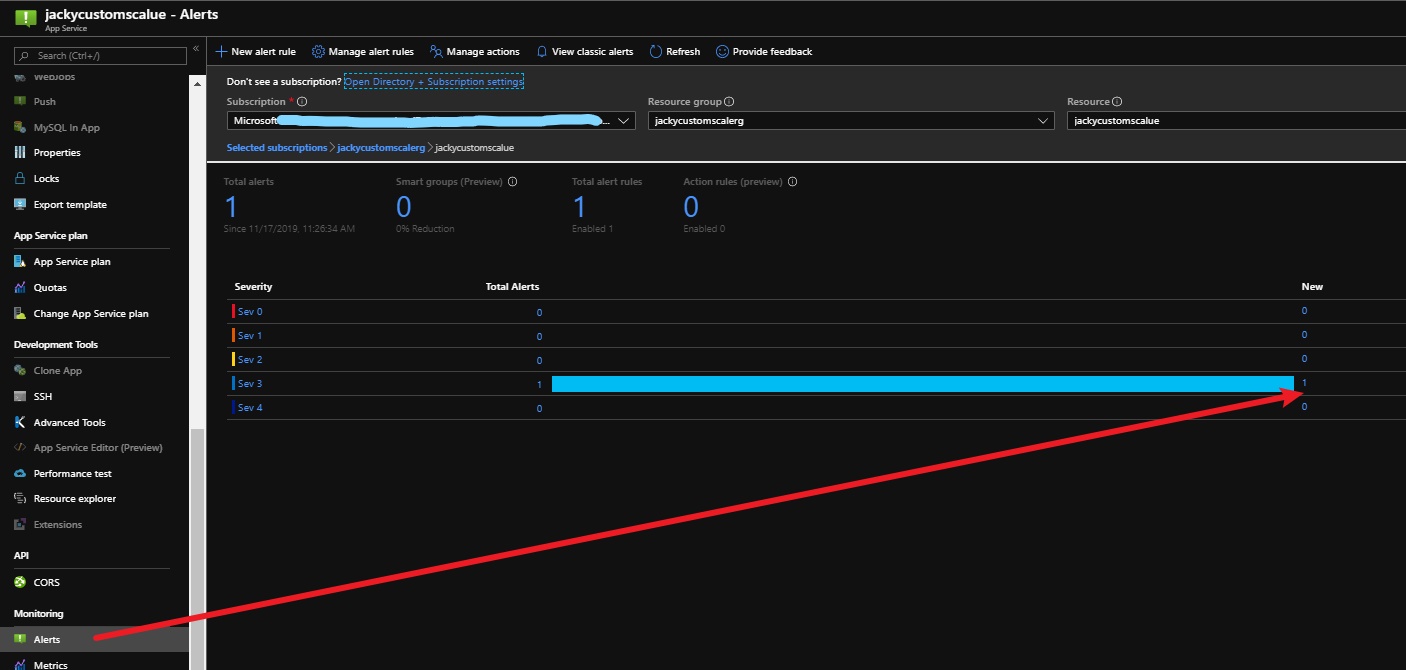
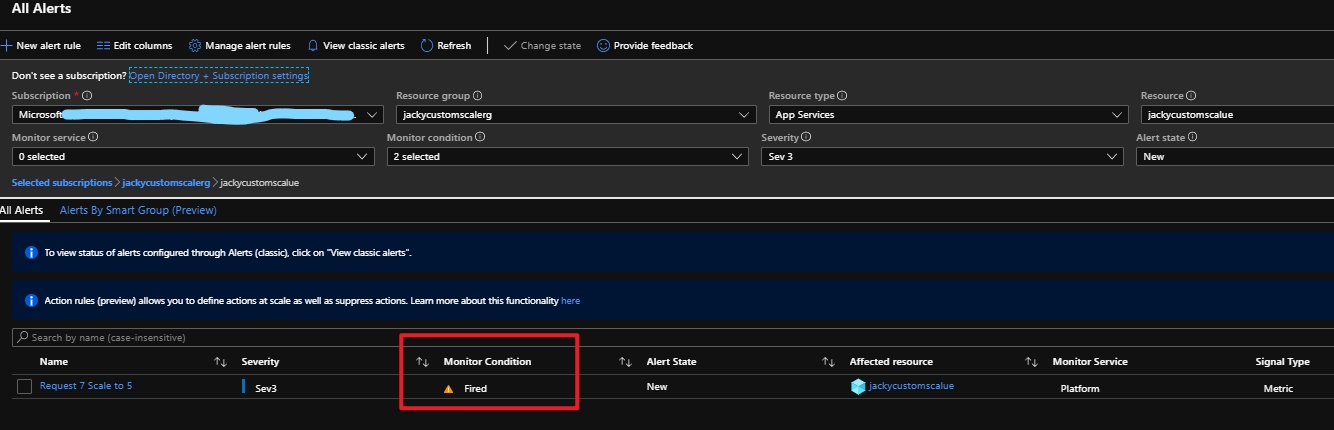
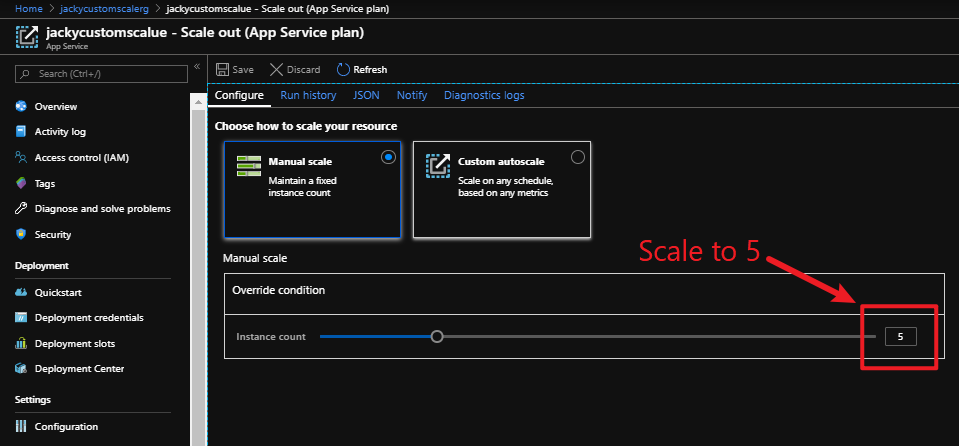
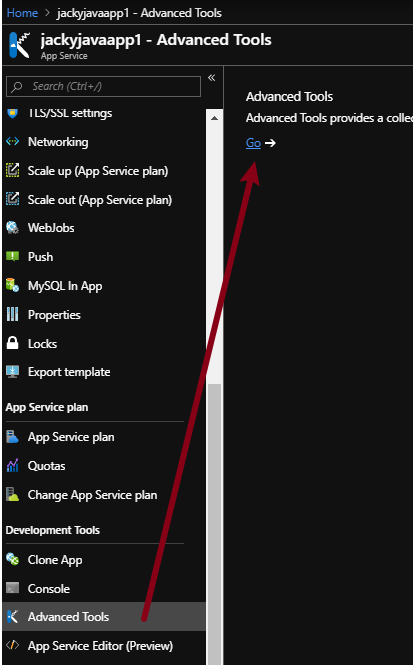
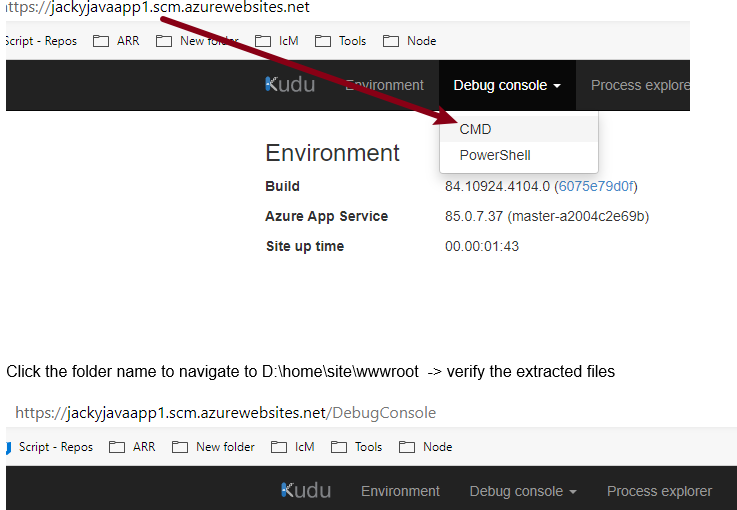
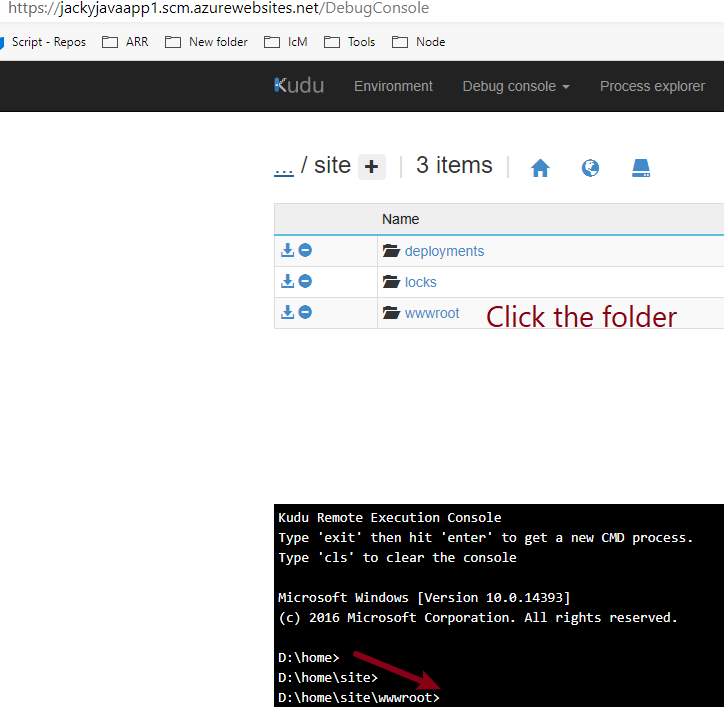
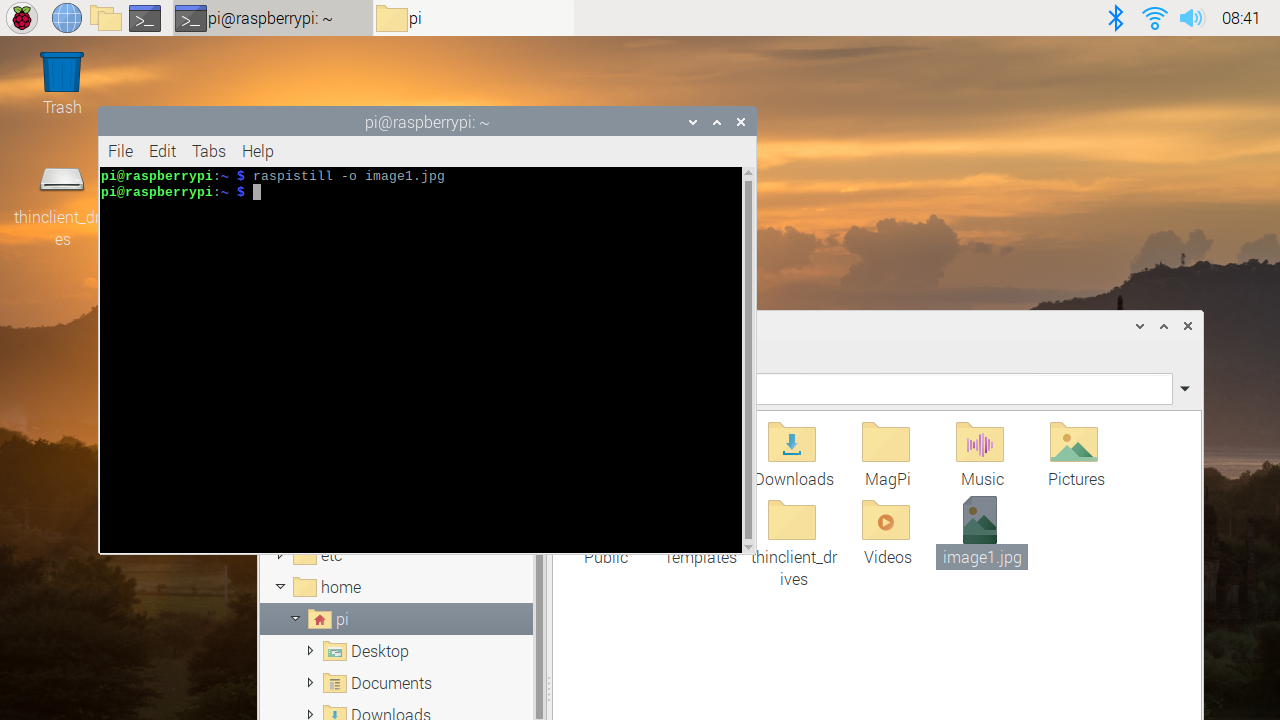
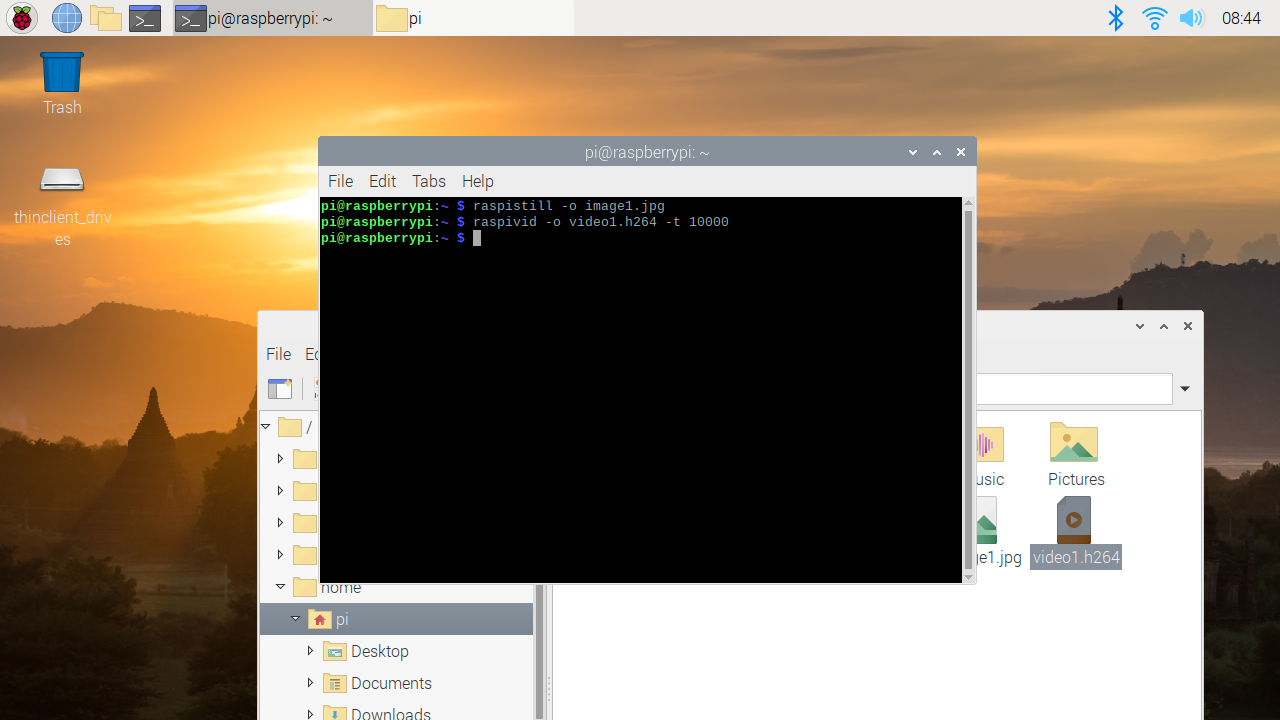
az storage blob show is the right way to get blob copy status. The command uses “Get Blob Properties” rest operation, which is the recommended approach: https://docs.microsoft.com/en-us/rest/api/storageservices/copy-blob.
It will show the copy properties of the last copy operation.
PS Azure:> az storage blob show –container-name dest1 –account-key “YourAccountKey” –account-name jackyst3 –name “MyVHD.vhd”
{
"content": "",
"deleted": false,
"metadata": {},
"name": "MyVHD.vhd",
"properties": {
"appendBlobCommittedBlockCount": null,
"blobTier": "Hot",
"blobTierChangeTime": null,
"blobTierInferred": true,
"blobType": "BlockBlob",
"contentLength": 0,
"contentRange": null,
"contentSettings": {
"cacheControl": null,
"contentDisposition": null,
"contentEncoding": null,
"contentLanguage": null,
"contentMd5": null,
"contentType": "application/octet-stream"
},
"copy": {
"completionTime": null,
"id": "a447e2f4-52bc-43e3-adfb-140c341b1208",
"progress": "201326592/570770310",
"source": "https://jackyst2.blob.core.windows.net/test/MyVHD.vhd?sp=r&st=2019-10-03T05:46:48Z&se=2019-10-03T13:46:48Z&spr=https&sv=2018-03-28&sig=nmQMfb6JmbgBdKSCmpifpDIn%2BZGHX9E4PFLWK1Gd%2B%2Bg%3D&sr=b",
"status": "pending",
"statusDescription": null
},
"creationTime": "2019-10-03T05:47:51+00:00",
"deletedTime": null,
"etag": "\"0x8D747C53A6C50CB\"",
"lastModified": "2019-10-03T05:47:51+00:00",
"lease": {
"duration": null,
"state": "available",
"status": "unlocked"
},
"pageBlobSequenceNumber": null,
"pageRanges": null,
"remainingRetentionDays": null,
"serverEncrypted": true
},
"snapshot": null
}
'''
PS Azure:\> az storage blob show --container-name dest1 --account-key "YourAccountKey" --account-name jackyst3 --name "MyVHD.vhd"
```json
{
"content": "",
"deleted": false,
"metadata": {},
"name": "MyVHD.vhd",
"properties": {
"appendBlobCommittedBlockCount": null,
"blobTier": "Hot",
"blobTierChangeTime": null,
"blobTierInferred": true,
"blobType": "BlockBlob",
"contentLength": 570770310,
"contentRange": null,
"contentSettings": {
"cacheControl": null,
"contentDisposition": null,
"contentEncoding": null,
"contentLanguage": null,
"contentMd5": null,
"contentType": "application/octet-stream"
},
"copy": {
"completionTime": "2019-10-03T05:49:50+00:00",
"id": "a447e2f4-52bc-43e3-adfb-140c341b1208",
"progress": "570770310/570770310",
"source": "https://jackyst2.blob.core.windows.net/test/MyVHD.vhd?sp=r&st=2019-10-03T05:46:48Z&se=2019-10-03T13:46:48Z&spr=https&sv=2018-03-28&sig=nmQMfb6JmbgBdKSCmpifpDIn%2BZGHX9E4PFLWK1Gd%2B%2Bg%3D&sr=b",
"status": "success",
"statusDescription": null
},
"creationTime": "2019-10-03T05:47:51+00:00",
"deletedTime": null,
"etag": "\"0x8D747C58189F762\"",
"lastModified": "2019-10-03T05:49:50+00:00",
"lease": {
"duration": null,
"state": "available",
"status": "unlocked"
},
"pageBlobSequenceNumber": null,
"pageRanges": null,
"remainingRetentionDays": null,
"serverEncrypted": true
},
"snapshot": null
}
'''
For more information:
https://github.com/Azure/azure-cli/issues/1787
HTH. Jacky 2019-10-3