https://news.microsoft.com/zh-tw/microsoft-reimagine-taiwan/
Customer-controlled storage account recovery (CSAR) is now live in Azure Portal
Updated 2021-6-26
Recover a deleted storage account
https://docs.microsoft.com/en-us/azure/storage/common/storage-account-recover
===============================================
How to recover a deleted Azure Storage Account:
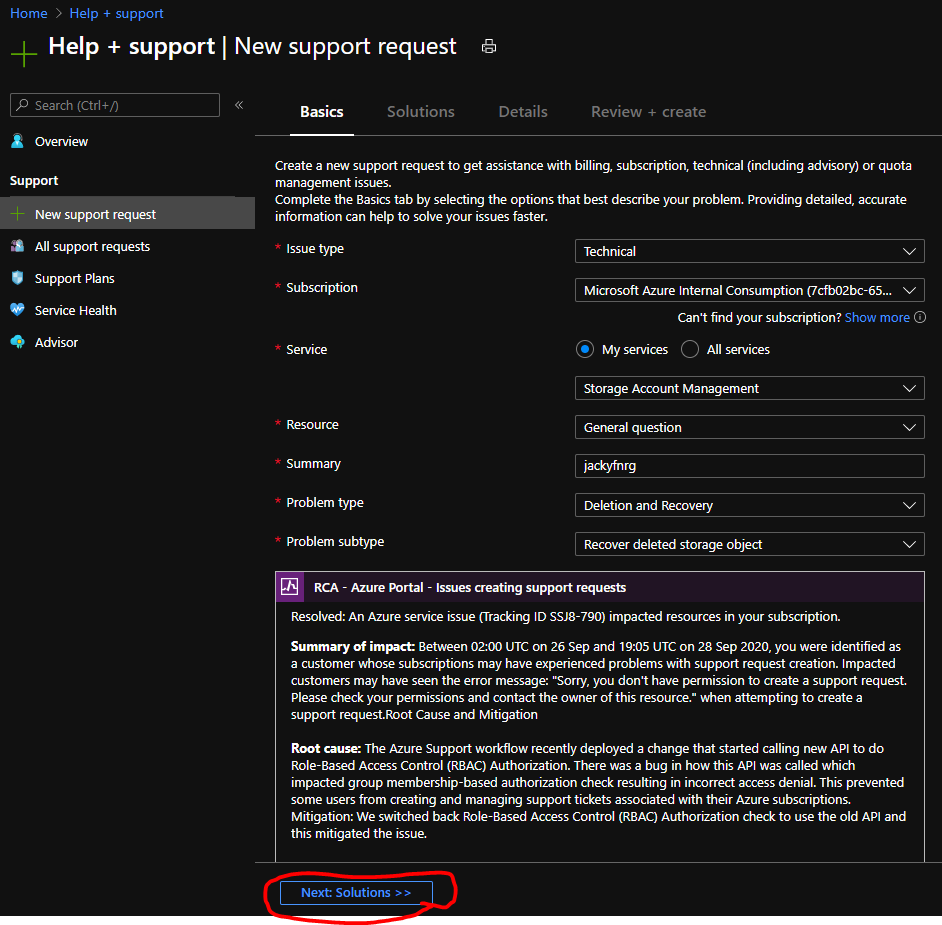
Navigate to the ‘New support request’ workflow
Select the appropriate options on the ‘Basics’ tab (see screenshot below) and navigate to the ‘Solutions’ tab
Click the ‘Recover a deleted storage account’ blade link on top of the solutions tab
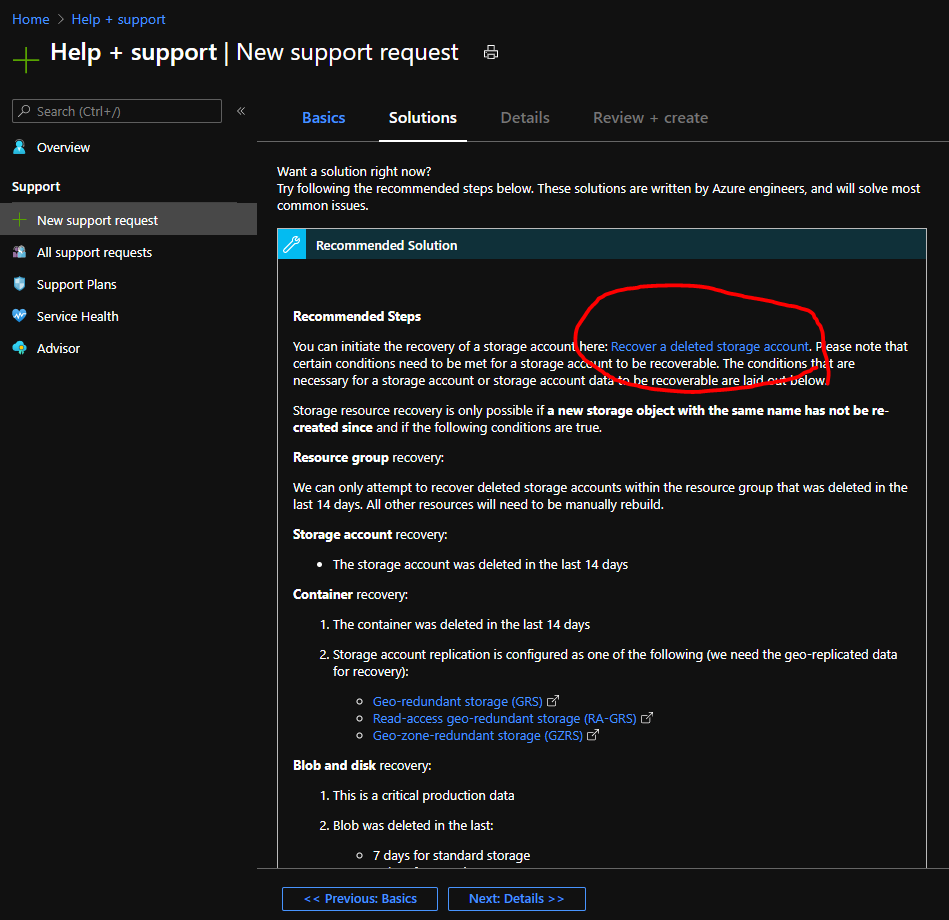
Select the deleted storage account you would like to recover from the dropdown and initiate the recovery process by clicking the button in the command bar at the bottom of the blade.
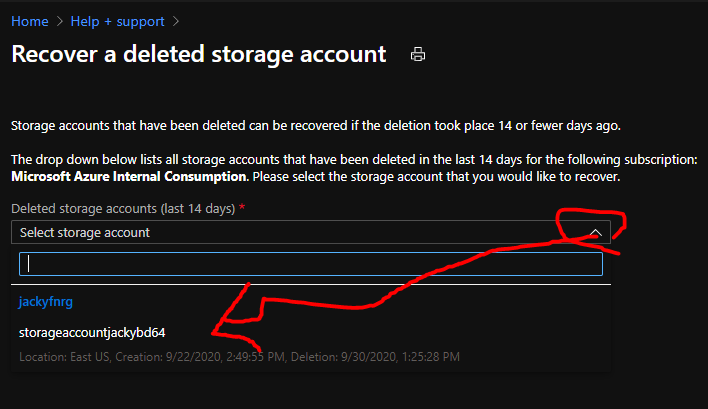
HTH. 2020-10-08 By Jacky
Prefetch Azure Service Bus messages is faster?
Prefetch speeds up the message flow by having a message readily available for local retrieval when and before the application asks for one. This throughput gain is the result of a trade-off that the application author must make explicitly:
With the ReceiveAndDelete receive mode, all messages that are acquired into the prefetch buffer are no longer available in the queue, and only reside in the in-memory prefetch buffer until they are received into the application through the Receive/ReceiveAsync or OnMessage/OnMessageAsync APIs. If the application terminates before the messages are received into the application, those messages are irrecoverably lost.
In the PeekLock receive mode, messages fetched into the Prefetch buffer are acquired into the buffer in a locked state, and have the timeout clock for the lock ticking. If the prefetch buffer is large, and processing takes so long that message locks expire while residing in the prefetch buffer or even while the application is processing the message, there might be some confusing events for the application to handle.
The application might acquire a message with an expired or imminently expiring lock. If so, the application might process the message, but then find that it cannot complete it due to a lock expiration. The application can check the LockedUntilUtc property (which is subject to clock skew between the broker and local machine clock). If the message lock has expired, the application must ignore the message; no API call on or with the message should be made. If the message is not expired but expiration is imminent, the lock can be renewed and extended by another default lock period by calling message.RenewLock()
If the lock silently expires in the prefetch buffer, the message is treated as abandoned and is again made available for retrieval from the queue. That might cause it to be fetched into the prefetch buffer; placed at the end. If the prefetch buffer cannot usually be worked through during the message expiration, this causes messages to be repeatedly prefetched but never effectively delivered in a usable (validly locked) state, and are eventually moved to the dead-letter queue once the maximum delivery count is exceeded.
If you need a high degree of reliability for message processing, and processing takes significant work and time, it is recommended that you use the prefetch feature conservatively, or not at all.
If you need high throughput and message processing is commonly cheap, prefetch yields significant throughput benefits.
The maximum prefetch count and the lock duration configured on the queue or subscription need to be balanced such that the lock timeout at least exceeds the cumulative expected message processing time for the maximum size of the prefetch buffer, plus one message. At the same time, the lock timeout ought not to be so long that messages can exceed their maximum TimeToLive when they are accidentally dropped, thus requiring their lock to expire before being redelivered.
For more information:
https://docs.microsoft.com/en-us/azure/service-bus-messaging/service-bus-prefetch
Sample Code:
1 | using Microsoft.Azure.ServiceBus; |
Test result:
1 | PS C:\Jacky\ServiceBusPrefetchTest\bin\Debug> .\ServiceBusPrefetchTest.exe |
HTH. 2020-9-29 By Jacky
Occasionally Receive Messages in Unexpected Sequence
Below sample code can reproduce it:
1 | using Microsoft.Azure.ServiceBus; |
Below sample code can prevent it:
1 | using Microsoft.Azure.ServiceBus; |
Collect X-Forward-For in Azure Web App
Create a web application and config Application Insights.
Telemetry initializer
1 | using Microsoft.ApplicationInsights.Channel; |
- Enable telemetry initializer for ASP.NET
1 | using Microsoft.ApplicationInsights.Extensibility; |
- Sending sample HTTP requests with X-Forwarded-For header or your custom header
1 | Invoke-WebRequest "https://jackywin3.azurewebsites.net/About" -Method GET -Headers @{"X-Forwarded-For" = "1.1.0.1"} |
- View the results of your telemetry initializer
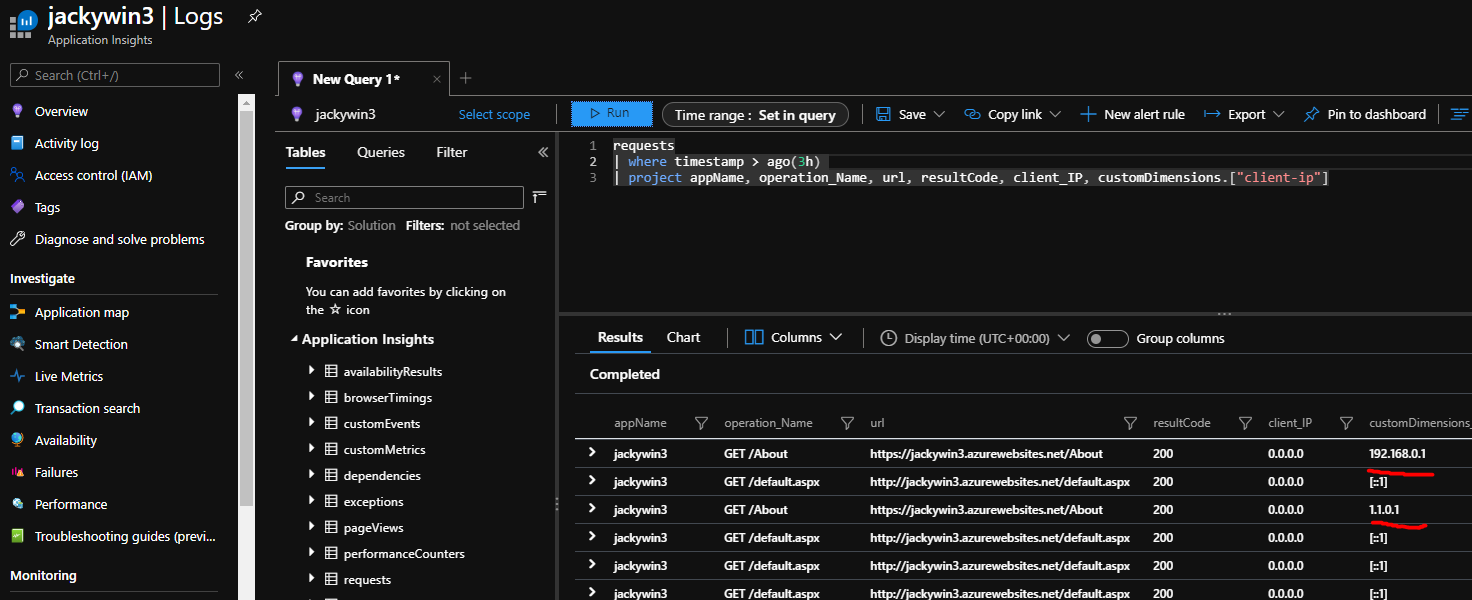
If you send new traffic to your site, and wait a few minutes. You can then run a query to confirm collection is working:
requests
| where timestamp > ago(1h)
| project appName, operation_Name, url, resultCode, client_IP, customDimensions.[“client-ip”]
For more information: https://docs.microsoft.com/en-us/azure/azure-monitor/app/ip-collection?tabs=net
Enjoy. 2020-9-23 By Jacky
Multiple issuers and openid-config API Management Service
1 | <policies> |
More Information: https://docs.microsoft.com/en-us/azure/api-management/api-management-access-restriction-policies#ValidateJWT
Enjoy. 2020-9-23 By Jacky
Windows 10 PowerToys
Microsoft PowerToys, a set of utilities for power users to tune and streamline your Windows 10 experience for greater productivity.
Install PowerToys: http://aka.ms/installpowertoys
Learn more in the PowerToys Wiki: http://aka.ms/powertoyswiki
PowerToys repo: https://aka.ms/powertoys
Enjoy. 2020-9-21 by Jacky
New Azure SQL Learning Tools - 2020 August
New Azure SQL Learning Tools help reduce the global technology skills gap
Azure SQL Fundamentals (aka.ms/azuresqlfundamentals) – a 6-course learning path on Microsoft Learn. This includes built-in sandbox environments and subscriptions
Azure SQL for beginners (aka.ms/azuresql4beginners) – a 61-video series which walks through all the content on the learning path and more.
Azure SQL Workshop (aka.ms/asqlworkshop, then select Workshop: Azure SQL) – a 1-2 day workshop including hands-on labs and slides which are free/open source for everyone to leverage.
Azure SQL Bootcamp (aka.ms/azuresqlbootcamp) –4-day (2 hours each day) live bootcamp from August 17-20.
Enjoy. 2020-Aug-21 by Jacky Chiou
Azure Cosmos DB Workshop
Two Day Suggested Schedule and includs PowerPoint Deck, .NET/Java Lab Guides
https://azurecosmosdb.github.io/labs/
Enjoy. 2020-Aug-18 By Jacky