有一個按兩下部署解決方案,用於使用 Logic App 備份 Azure 防火牆和防火牆策略。此解決方案在 Github 存儲庫中提供:Azure-Network-Security/Azure Firewall/Template - Logic App for Azure Firewall Backups
https://github.com/Azure/Azure-Network-Security/tree/master/Azure%20Firewall/Template%20-%20Logic%20App%20for%20Azure%20Firewall%20Backups
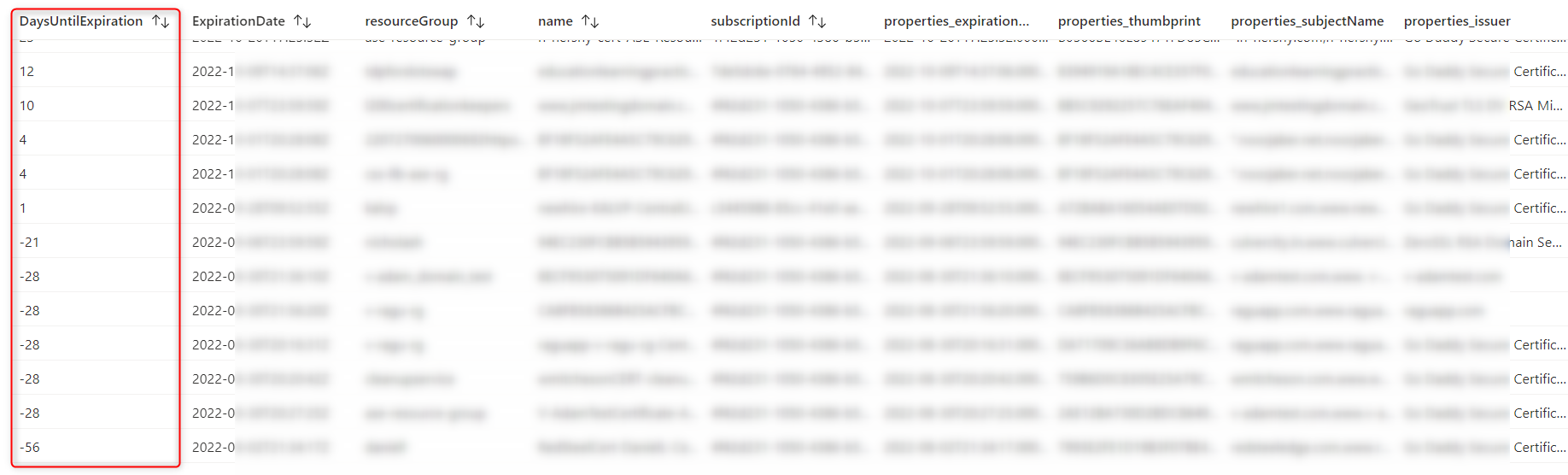
Logic App 已配置並計劃為每三天運行一次「備份防火牆和防火牆策略」,並將其存儲在創建的存儲帳戶中。我們可以根據需要修改此頻率。備份檔按時間順序排列的。
我們可以從存儲帳戶容器下載此備份(json 檔),並使用 cloud shell 的以下命令將其還原:
New-AzResourceGroupDeployment -name -ResourceGroupName -TemplateFile
此還原將要求提供兩個輸入,FirewallPublicIP 和 FirewallVnet:我們可以提供這些輸入,如下所示:
/subscriptions/YourSubscriptionId/resourceGroups/CxE-AzFWBackup-WebinarDemo/providers/Microsoft.Network/publicIPAddresses/FWPIPBDemo
/subscriptions/YourSubscriptionId/resourceGroups/CxE-AzFWBackup-WebinarDemo/providers/Microsoft.Network/virtualNetworks/AzFwVnet
此還原命令將從備份中同時還原防火牆和防火牆策略,即使它們已被刪除也是如此。通過選擇要還原的相應備份檔,此還原命令可以返回到特定日期的狀態。
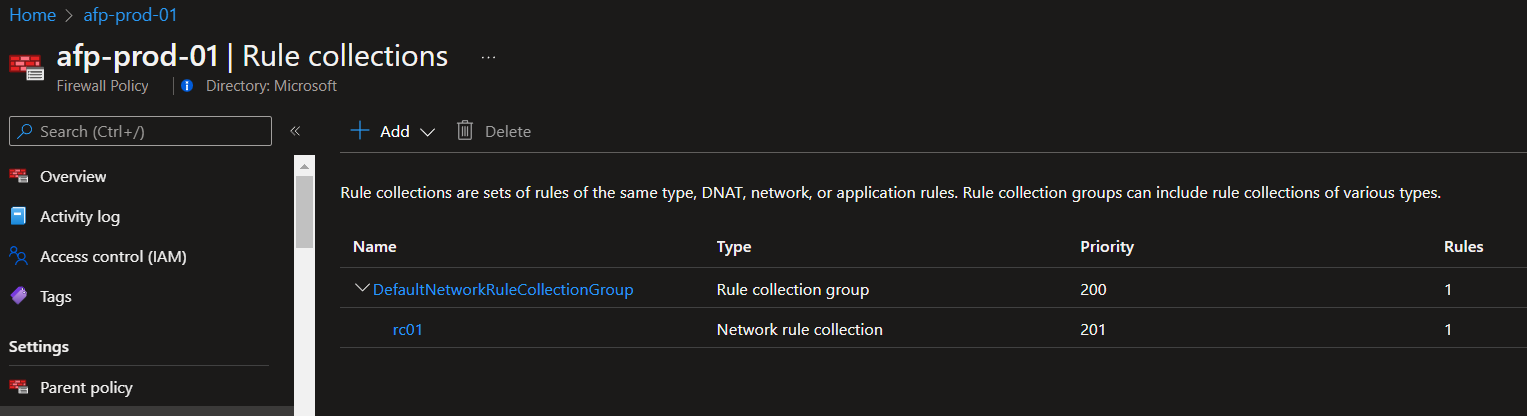
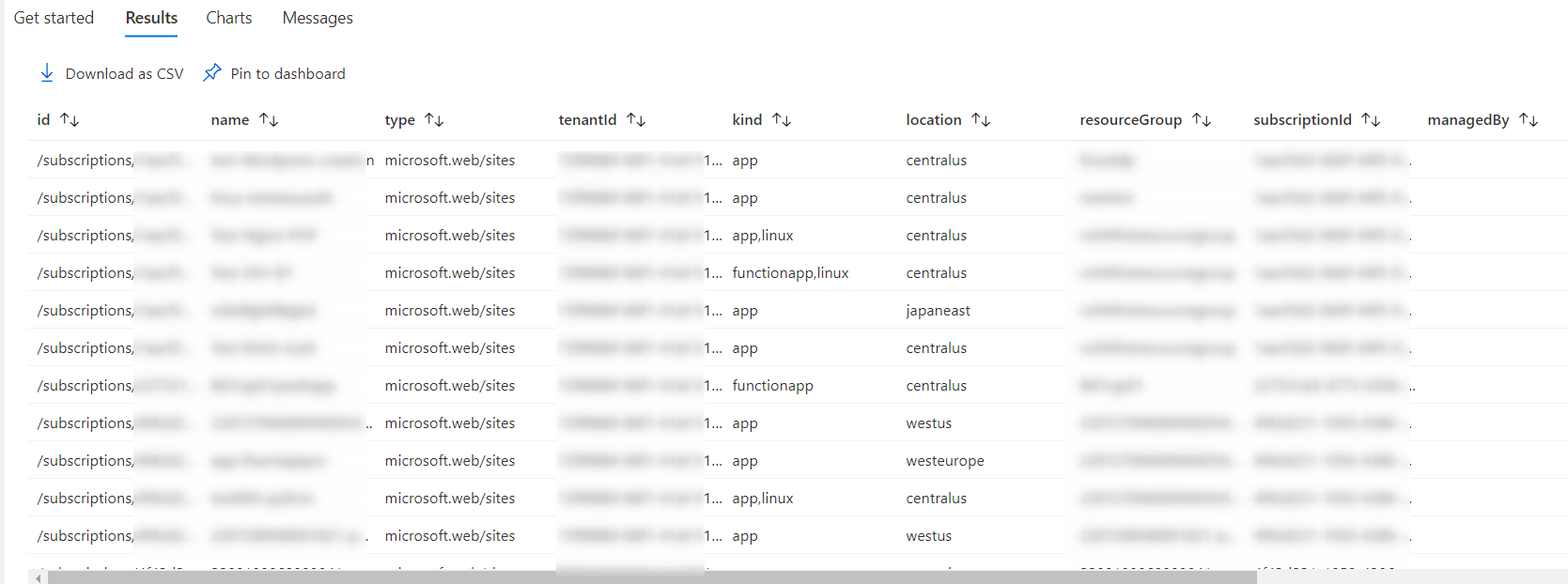
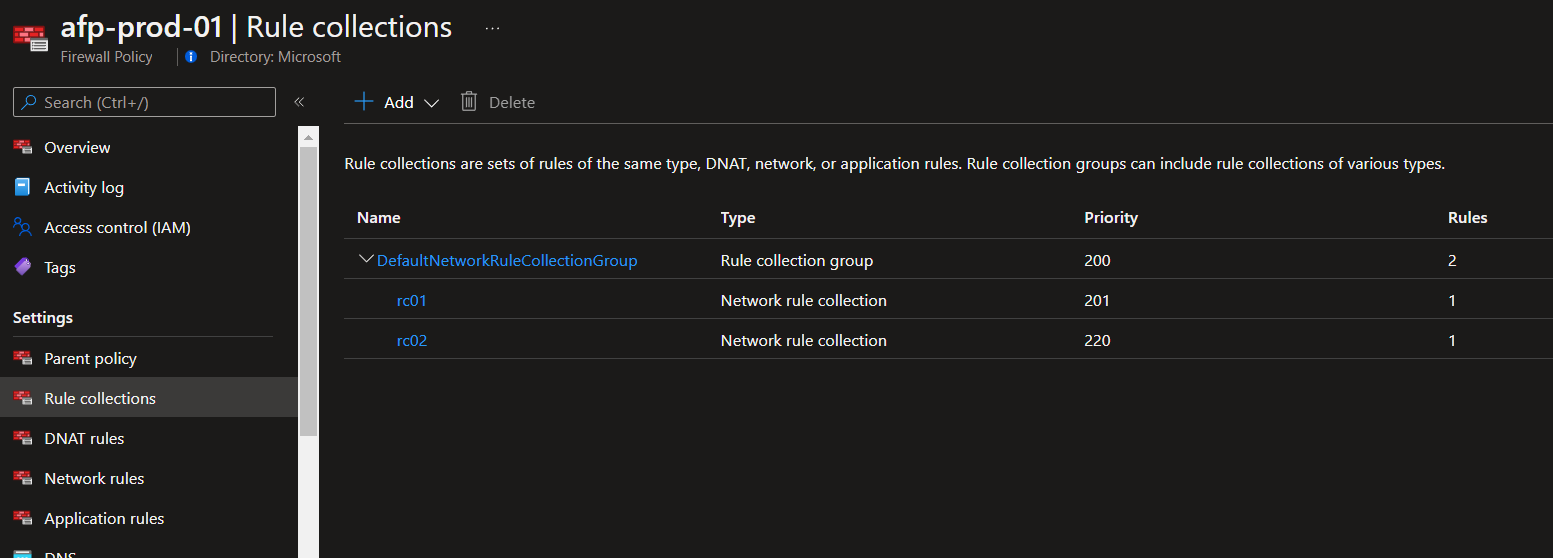
在測試環境裡加入 rc02 如下圖:
PS /home/jacky> New-AzResourceGroupDeployment -name AzureFirewall_vhub-prod-jpe -ResourceGroupName rg-lab-candel -TemplateFile “backup-2022-08-22T09_24_01.1439684Z”
virtualHubs_vhub_prod_jpe_externalid: /subscriptions/YourSubscriptionId/resourceGroups/rg-lab-candel/providers/Microsoft.Network/virtualHubs/vhub-prod-jpe
DeploymentName : AzureFirewall_vhub-prod-jpe
ResourceGroupName : rg-lab-candel
ProvisioningState : Succeeded
Timestamp : 8/22/2022 10:02:52 AM
Mode : Incremental
執行還原的指令後, 還原 只有備份檔內的 rc01 , 如下圖: